The main goal of our Cyber Initiative is to build a more capable cyber policy field that works with the private sector, as well as government, to solve pressing challenges. As we reached the midpoint of our initial five-year funding commitment, we thought it was time to look at how we’re doing.
With that in mind, last year we commissioned strategy consultants Camber Collective, with input from Cyber experts Upturn, to evaluate our grantmaking to date. After conducting more than 30 interviews with experts from across the network, Camber Collective provided us with an evaluation and recommendations that will help us refine and improve our grantmaking strategy moving forward.
For those working in the field, or interested in building capacity in other realms, I encourage you to read the whole report. Here are some of the most important things we learned from it, and what we’re planning to do differently going forward.
Communicating policy ideas and solutions is hard
As one interviewee from academia who recently worked in government stated, “the idea that academics will [simply] publish or blog about their work and influence policy is laughable.” Research is most effective when it is: (i) policy-driven, (ii) backed by a diverse group of authors known to policymakers, (iii) timely, (iv) clearly translates new data and findings into policy implications, and (v) is linked to broader paths of exposure including media. Although there are examples of this sort of research from the field and Cyber Initiative’s grantees, it still happens too rarely.
Most of the research Camber Collective saw in the field appears to lack several of the characteristics often cited as critical to informing policy. Even one of the grantees that both Camber Collective and I deem more successful at creating policy-relevant research noted that “we publish a ton of stuff, but most of it isn’t widely read [in government]”. These challenges are by no means unique to academia (or this field), although academia is where the gap between research and informing cyber policy appears largest. Under condition of confidentially, multiple think tank and advocacy organizations also conceded that their work is often not absorbed by policymakers.
A common finding in the evaluation was that for the field to grow and truly inform policy, it needs more “translators” and “connectors” individuals with experience, insights and credibility in government and/or corporate policy as well as technical issues. These are experts with not just the right knowledge, but even more importantly the type of large professional networks necessary to make new introductions, engender trust, and inform policy. This type of individual is not just important as a “translator” between industries, but also as a network builder and “connector” who is just as likely to link an interested party with another expert as they are to answer questions themselves. Per many, the most important phrase in the emerging network of cyber experts is not “I can help you” but rather “you know who you should really talk to is…”
Going forward, one focus of our grantmaking will be on building translation infrastructure to make cyber policy ideas and solutions more understandable and accessible to key decision-makers. That means, among other things, focusing on the ability of institutions and individuals to communicate their ideas to policymakers, both directly and through the media. It also means support for the journalists and media platforms who need to understand and explain a technically complex subject in their reporting. In the same way we’re thinking about building institutional and individual capacity to act as translators, we’re also thinking about what we’re calling narrative capacity—the frames, narratives, metaphors and images that will help policymakers and the broader public really understand the stakes, the actors and their motivations, and the deeper democratic values implicated in many cyber policy debates.
Core institutions needed to bridge gaps
Another key finding in the evaluation is the existence of some serious gaps between the various stakeholder groups—a distinct lack of trust, as well as of institutional and individual connections—observations that I suspect will ring true to anyone who has worked on cyber policy. The most prominent gaps exist between information privacy and civil liberties advocacy groups and national security practitioners, and between much of academia and policymakers in general. Both evaluation interviews and map data gathering revealed these gaps.
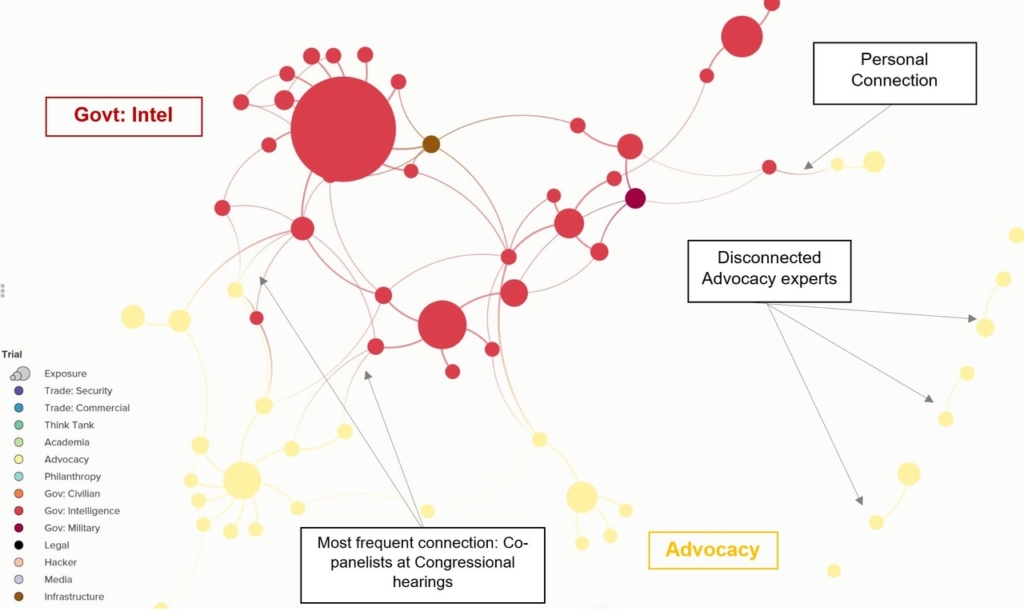
This first map shows how U.S. government security agencies (in red) are quite disconnected from civil liberties and advocacy groups (in yellow).
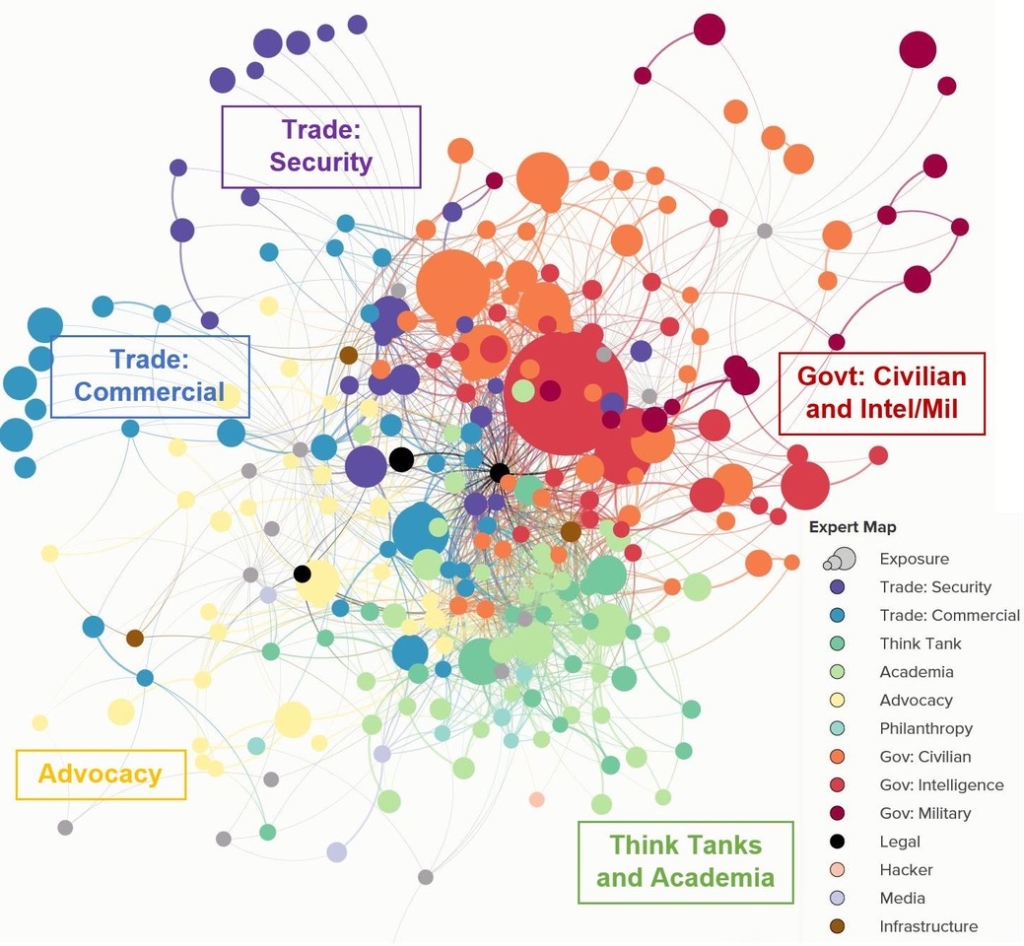
The second map shows how academia (in light green) is not well-connected to policymakers (in orange). It also shows national security and advocacy groups on different sides of the overall network map, reinforcing the notion that they are not well-connected.
Another point that these maps bring home is the dearth of core civil society institutions with a cyber policy footprint large enough to be able to weigh in on issues across the whole range of domains where cyber is becoming increasingly important. In other words, it’s not just the individual connectors and translators that are needed, but homes for them of sufficient size and sophistication on these issues to help fill the gaps and strengthen the overall cyber policy landscape.
Going forward, we plan to support the development of key civil society institutions that can serve as centers of gravity within the cyber policy ecosystem—homes for individual experts and network nodes supporting stronger connections among the various stakeholder groups in the system.
We also plan to focus more on helping emerging interdisciplinary scholars succeed in academia and beyond. One option is to fund more fellowships in government for young experts who can gain much-needed experience and insight into how to make academic research and education relevant for policymaking. Our three anchor grantees—UC Berkeley, MIT and Stanford—remain critical to our success, especially in the education of new translators and connectors. The importance of those cross-functional individuals make sense the new educational programs they are developing being should – over time – develop new talent in this area.
Finally, we’re also reflecting on the evaluation’s suggestion that we find better ways to use public opinion and broadcasting of information to inform the policy debate. We see this as part of the larger need for improved translation infrastructure—building the capacity of key institutions and individuals on both the supply and demand sides of the equation, and supporting innovative thinking into the underlying narratives about cybersecurity that will help both policymakers and the public understand this critical issue.
With the results of this evaluation in hand, we’ll be adjusting our grantmaking to focus on places where we think we can have the greatest impact. If you have thoughts on where we should take the Cyber Initiative, we’d love to hear from you.


